Encrypted Password Database Help Page

Multi User Access
You can grant other users access to an encrypted password database using an RSA public key or exported smart card cert file.Using an RSA key or smart card eliminates the need to have a single shared password or symmetric key file. This allows for user groups to access the database with each user that has access bound to RSA key or smart card.
For automation systems and application accounts can be granted RSA key access so passwords can be retrieved from an encrypted database rather than storing passwords in scripts or configuration files.
To add authorized users to an encrypted database click on the User menu and select the Add Users option. This will display the Add User For Database Access dialog:
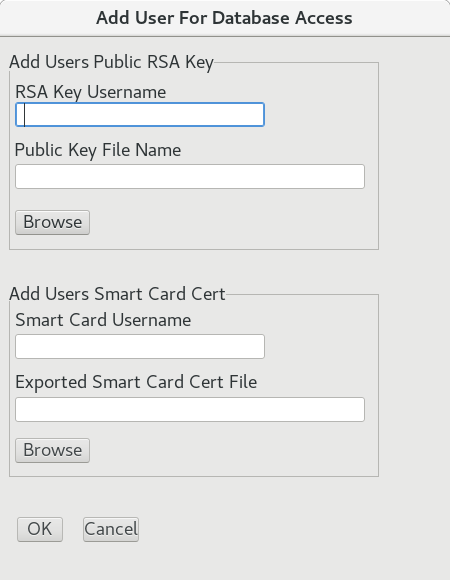
In the Add User For Database Access dialog Use one of the 2 methods for adding users:
RSA Public Key
In the Add Users Public RSA Key section input a username for the user you are adding. Click on the Browse button and select the public key file the user has provided to you. Click on the OK button to add the user.Smart Card Cert
In the Add Users Smart Card Cert section input a username for the user you are adding. Click on the Browse button and select the exported smart card cert file the user has provided to you. Click on the OK button to add the user.For smart card users you can export a public cert using the p11tool. For CAC users run the following command to export your public cert:
> p11tool --list-all-certsThe output should look like the following:
warning: no token URL was provided for this operation; the available tokens are: pkcs11:model=p11-kit-trust;manufacturer=PKCS%2311%20Kit;serial=1;token=System%20Trust pkcs11:model=p11-kit-trust;manufacturer=PKCS%2311%20Kit;serial=1;token=Default%20Trust pkcs11:model=PKCS%2315%20emulated;manufacturer=piv_II;serial=3271a1843390d7f3;token=LASTNAME.FIRSTNAME.MIDDLENAME.0000000000Run the following command to list available certs for all objects:
> p11tool --list-all-certs 'pkcs11:model=PKCS%2315%20emulated;manufacturer=piv_II;serial=0000000000000000;token=LASTNAME.FIRSTNAME.MIDDLENAME.0000000000’Where the input is the PIV string with the user's name and CAC ID number.
The output should look like the following:
Object 0: URL: pkcs11:model=PKCS%2315%20emulated;manufacturer=piv_II;serial=0000000000000000;token=LASTNAME.FIRSTNAME.MIDDLENAME.0000000000;id=%01;object=Certificate%20for%20PIV%20Authentication;type=cert Type: X.509 Certificate (RSA-2048) Expires: Sat Jul 1 23:59:59 2023 Label: Certificate for PIV Authentication ID: 01 ... ...NOTE: Some CAC cards will only have 1 or 2 Objects and others will have 4 or more. The main object you need is labeled:
Certificate for PIV Authentication
Next you will need to export the ‘Certificate for PIV Authentication’ using the following command example:
> p11tool --export 'pkcs11:model=PKCS%2315%20emulated;manufacturer=piv_II;serial=0000000000000000;token=LASTNAME.FIRSTNAME.MIDDLENAME.0000000000;id=%01;object=Certificate%20for%20PIV%20Authentication;type=cert’This display a PEM formatted certificate that looks like the following example:
-----BEGIN CERTIFICATE----- MIIFQzCCBCugAwIBAgIEAhEqlTANBgkqhkiG9w0BAQsFADBaMQswCQYDVQQGEwJV ... ... P9esiAzLmQ== -----END CERTIFICATE-----Copy the PEM output to a .pem text file. The .pem file will be the smart card used for access to the encrypted database.
Listing Users
To list users with access to the database click on the Users Menu and select List users:
A status window will be displayed listing all the users and type of access.
Removing Users
To remove a user from the database click on the Users Menu and select Remove Users. An input dialog box will appear prompting you to enter the username to remove.Updating Users
If a user get a new smart card or RSA key you must remove the user and add them back.Return to Help Pages Contents